iFrame security settings
You can embed the Signing Flow of a Signature Request into your web application using an iFrame. This allows Signers to complete the process without leaving your site or application.
- In Sandbox, embedding is always allowed.
- In Production, you must configure security settings to control where embedding is permitted.
iFraming in Sandbox
In the Sandbox environment, embedding the Signing Flow via iFrame is always permitted if the following query parameter is added: disable_domain_validation.
This parameter works only in the Sandbox environment and allows you to bypass all CSP (Content Security Policy) verifications so you can test your integration in no time, without restriction. When used, it returns the following header:
Content-Security-Policy: frame-ancestors *;This allows the Signing Flow to be embedded in any domain, regardless of the parent or embedding origin.
Before going live and using our Production environment, we strongly encourage you to test your iFraming rules without thedisable_domain_validation parameter in Sandbox. This lets you validate your configuration and avoid surprises when going live.
iFraming in Production
In Production, embedding the Signing Flow is restricted for security reasons. You must explicitly configure how and where the Signing Flow can be embedded.
Go to your iFraming settings page to manage your settings.
This setting page is only accessible to Owners and Admins.
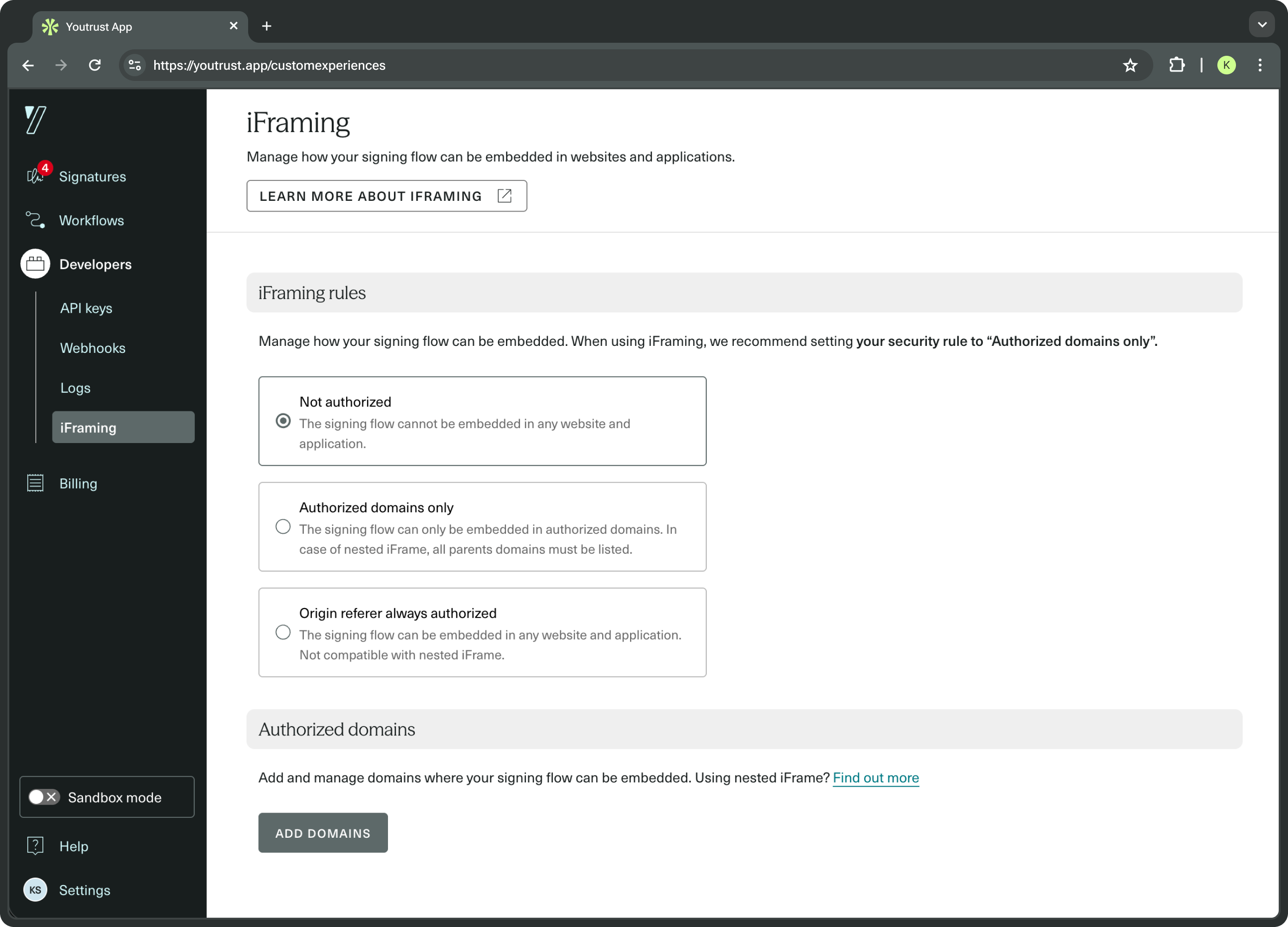
Available options
You must choose one of the following security modes:
1. Not authorized (default)
The Signing Flow cannot be embedded in any website or application.
2. Authorized domains only
The Signing Flow can only be embedded from domains you explicitly list. It is the recommended option for most use cases. It also supports nested iframes, provided all parent domains are listed.
To authorize domains:
- Open the iFraming settings page.
- Click "Add domains".
- Enter domains to authorize.
- Click on "Confirm" to save the domains added.
Domains can optionally start with a * to represent a wildcard subdomain
Examples of valid domains:
https://your-app.com
https://clientportal.your-app.com
https://*.your-app.com3. Origin referer always authorised
Allows embedding from any website or application as long as a Referer header is present.
This option is not compatible with nested iframes. It should be used only if you cannot restrict iFraming to specific domains.
Updated 12 days ago